"威瑞森数据报告"相关数据
更新时间:2022-01-28进入8月后,2020年已经进入下半场,回顾前7个月的剧集市场表现,内容亮点多多。《清平乐》《三生三世枕上书》领衔古装剧市场,《新世界》《龙岭迷窟》《隐秘的角落》等悬疑剧精彩连连,《安家》《三十而已》等现实题材热播剧话题热度引爆全网,《下一站是幸福》《冰糖炖雪梨》《传闻中的陈芊芊》等爱情甜宠剧收割大批少女心。“好内容背后潜藏巨大商业价值”,在国产剧制作水平及用户口碑不断提升的利好趋势下,“剧集”逐渐成为品牌营销的“座上宾”,大剧营销市场显现出强劲的发展势头。
在剧集营销市场不断进发的趋势下,艺恩基于营销智库的软广数据监测,发布《2020大剧营销数据简报》,快速复盘2020剧集营销领域品牌主软广投放的市场表现、内容偏好、品类品牌投放集中度等,以期窥探剧集营销发展的新风向。
 2020年中国刘昊然与vivo用户重合度-地域的情况该统计数据包含了2020年中国刘昊然与vivo用户重合度-地域的情况。其中,刘昊然与vivo用户在河南的重合度为16119。2020年发布时间:2020-12-02
2020年中国刘昊然与vivo用户重合度-地域的情况该统计数据包含了2020年中国刘昊然与vivo用户重合度-地域的情况。其中,刘昊然与vivo用户在河南的重合度为16119。2020年发布时间:2020-12-02 2020年中国刘昊然与vivo用户重合度-年龄的情况该统计数据包含了2020年中国刘昊然与vivo用户重合度-年龄的情况。其中,刘昊然与vivo用户年龄在18-24岁的重合度为79488。2020年发布时间:2020-12-02
2020年中国刘昊然与vivo用户重合度-年龄的情况该统计数据包含了2020年中国刘昊然与vivo用户重合度-年龄的情况。其中,刘昊然与vivo用户年龄在18-24岁的重合度为79488。2020年发布时间:2020-12-02 2008-2009年第一季度中国电影市场数据该统计数据包含了2008-2009年第一季度中国电影市场数据。其中2009年第一季度票房为125500万元。2008-2009年发布时间:2021-01-22
2008-2009年第一季度中国电影市场数据该统计数据包含了2008-2009年第一季度中国电影市场数据。其中2009年第一季度票房为125500万元。2008-2009年发布时间:2021-01-22 2015-2017年Q3中国艺人经纪行业公司欢瑞世纪营业利润情况该统计数据包含了2015-2017年Q3中国艺人经纪行业公司欢瑞世纪营业利润情况。2017年Q3营业利润为14.61百万元。2015-2017年发布时间:2020-06-27
2015-2017年Q3中国艺人经纪行业公司欢瑞世纪营业利润情况该统计数据包含了2015-2017年Q3中国艺人经纪行业公司欢瑞世纪营业利润情况。2017年Q3营业利润为14.61百万元。2015-2017年发布时间:2020-06-27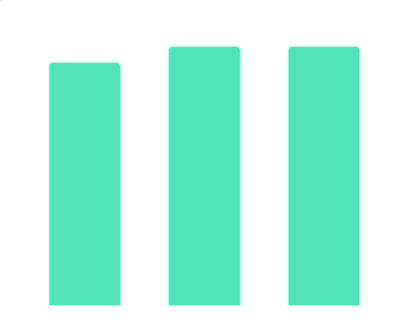 2017年中国各规模影院运营数据情况该统计数据包含了2017年全国各规模影院运营数据情况。2017年全国大型影院(8-10厅)平均单日单厅票房为4380.0元。2017年发布时间:2020-07-16
2017年中国各规模影院运营数据情况该统计数据包含了2017年全国各规模影院运营数据情况。2017年全国大型影院(8-10厅)平均单日单厅票房为4380.0元。2017年发布时间:2020-07-16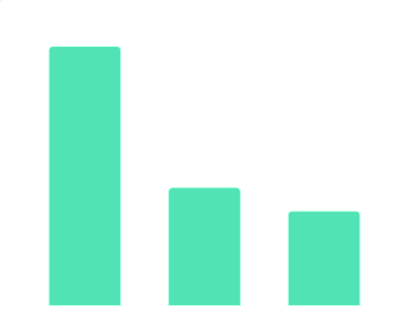 2019年10月中国教育行业融资地域数据该统计数据包含了2019年10月中国教育行业融资地域数据。2019年10月中国北京教育行业融资公司数量达11家。2019年发布时间:2019-11-08
2019年10月中国教育行业融资地域数据该统计数据包含了2019年10月中国教育行业融资地域数据。2019年10月中国北京教育行业融资公司数量达11家。2019年发布时间:2019-11-08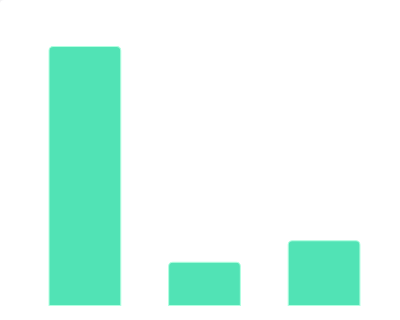 2019年10月中国教育行业融资体量数据该统计数据包含了2019年10月中国教育行业融资体量数据。2019年10月中国教育行业融资体量数千万的公司数量达12家。2019年发布时间:2019-11-08
2019年10月中国教育行业融资体量数据该统计数据包含了2019年10月中国教育行业融资体量数据。2019年10月中国教育行业融资体量数千万的公司数量达12家。2019年发布时间:2019-11-08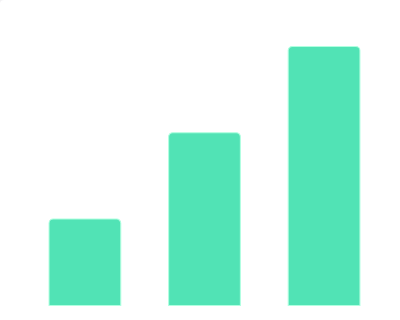 2019年10月中国教育行业融资轮次数据该统计数据包含了2019年10月中国教育行业融资轮次数据。有5家公司获得了A轮融资,6家公司获得了战略融资。2019年发布时间:2019-11-08
2019年10月中国教育行业融资轮次数据该统计数据包含了2019年10月中国教育行业融资轮次数据。有5家公司获得了A轮融资,6家公司获得了战略融资。2019年发布时间:2019-11-08 2019年10月中国教育行业细分领域融资数据该统计数据包含了2019年10月中国教育行业细分领域融资数据。2019年10月中国教育行业STEAM领域融资公司数量达9个。2019年发布时间:2019-11-08
2019年10月中国教育行业细分领域融资数据该统计数据包含了2019年10月中国教育行业细分领域融资数据。2019年10月中国教育行业STEAM领域融资公司数量达9个。2019年发布时间:2019-11-08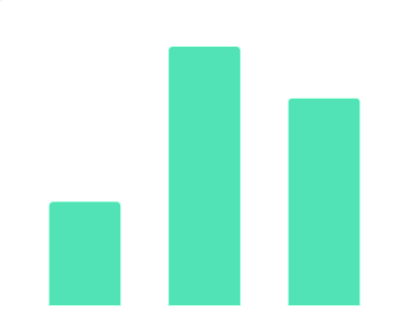 2019年11月中国教育行业融资体量数据该统计数据包含了2019年11月中国教育行业融资体量数据。2019年11月中国教育行业融资体量为数千万的公司数量达10家。2019年发布时间:2019-12-12
2019年11月中国教育行业融资体量数据该统计数据包含了2019年11月中国教育行业融资体量数据。2019年11月中国教育行业融资体量为数千万的公司数量达10家。2019年发布时间:2019-12-12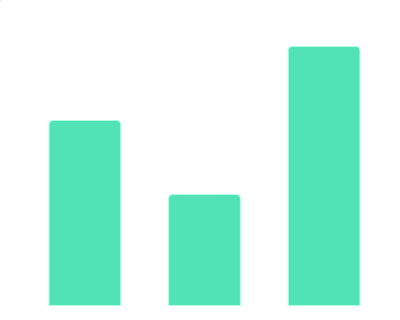 2019年11月中国教育行业融资轮次数据该数据包含了2019年11月中国教育行业融资轮次数据。股权融资公司数量为16家。2019年发布时间:2019-12-12
2019年11月中国教育行业融资轮次数据该数据包含了2019年11月中国教育行业融资轮次数据。股权融资公司数量为16家。2019年发布时间:2019-12-12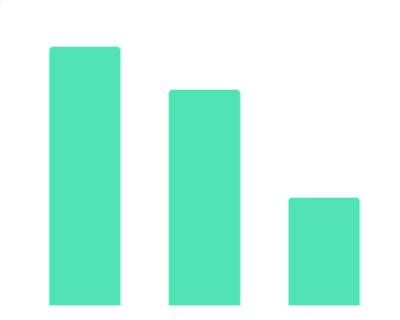 2019年11月中国教育行业融资地域分布数据该统计数据包含了2019年11月中国教育行业融资地域分布数据。北京地区教育行业获得融资的公司数量为12家。2019年发布时间:2019-12-12
2019年11月中国教育行业融资地域分布数据该统计数据包含了2019年11月中国教育行业融资地域分布数据。北京地区教育行业获得融资的公司数量为12家。2019年发布时间:2019-12-12 2018年-2021年中国各大视频平台剧综入围播映指数TOP10个数占比该统计数据包含了2018年-2021年中国各大视频平台剧综入围播映指数TOP10个数占比。腾讯在剧集上的表现更出色,而爱奇艺则在综艺上的播放量占比更高。2018-2021年发布时间:2021-11-19
2018年-2021年中国各大视频平台剧综入围播映指数TOP10个数占比该统计数据包含了2018年-2021年中国各大视频平台剧综入围播映指数TOP10个数占比。腾讯在剧集上的表现更出色,而爱奇艺则在综艺上的播放量占比更高。2018-2021年发布时间:2021-11-19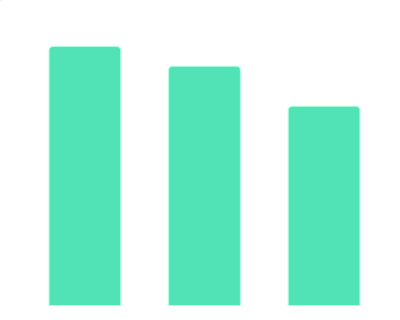 2019年11月中国教育行业融资细分领域数据该统计数据包含了2019年11月中国教育行业融资细分领域数据。2019年11月中国教育行业K12领域融资公司数量达13家。2019年发布时间:2019-12-12
2019年11月中国教育行业融资细分领域数据该统计数据包含了2019年11月中国教育行业融资细分领域数据。2019年11月中国教育行业K12领域融资公司数量达13家。2019年发布时间:2019-12-12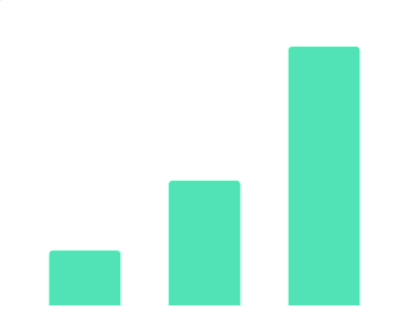 2013-2019年数据服务领域投资事件情况该统计数据包含了2013-2019年数据服务领域投资事件情况。2019年数据服务领域投资事件数量为40起。2013-2019年发布时间:2019-05-13
2013-2019年数据服务领域投资事件情况该统计数据包含了2013-2019年数据服务领域投资事件情况。2019年数据服务领域投资事件数量为40起。2013-2019年发布时间:2019-05-13 2009年中国观影观众性别分布情况该统计数据包含了2009年中国观影观众性别分布情况。男性占比最高,占比50.5%。2009年发布时间:2020-08-12
2009年中国观影观众性别分布情况该统计数据包含了2009年中国观影观众性别分布情况。男性占比最高,占比50.5%。2009年发布时间:2020-08-12 2009年中国观影观众年龄分布情况该统计数据包含了2009年中国观影观众年龄分布情况。26-30岁的占比最高,占比26.6%。2009年发布时间:2020-08-14
2009年中国观影观众年龄分布情况该统计数据包含了2009年中国观影观众年龄分布情况。26-30岁的占比最高,占比26.6%。2009年发布时间:2020-08-14 2009年中国观影观众省市分布情况该统计数据包含了2009年中国观影观众省市分布情况。其他城市的占比最高,占比37.9%。2009年发布时间:2020-08-14
2009年中国观影观众省市分布情况该统计数据包含了2009年中国观影观众省市分布情况。其他城市的占比最高,占比37.9%。2009年发布时间:2020-08-14 2009年中国观影观众的婚姻状况分布情况该统计数据包含了2009年中国观影观众的婚姻状况分布情况。未婚的占比最高,占比53.9%。2009年发布时间:2020-08-12
2009年中国观影观众的婚姻状况分布情况该统计数据包含了2009年中国观影观众的婚姻状况分布情况。未婚的占比最高,占比53.9%。2009年发布时间:2020-08-12 2009年中国观影观众的教育程度分布情况该统计数据包含了2009年中国观影观众的教育程度分布情况。大学本科的占比最高,占比45.1%。2009年发布时间:2020-08-14
2009年中国观影观众的教育程度分布情况该统计数据包含了2009年中国观影观众的教育程度分布情况。大学本科的占比最高,占比45.1%。2009年发布时间:2020-08-14





