"2021年数据泄露调查报告"相关数据
更新时间:2024-10-292019年数据泄露调查报告
Introduction
The statements you will read in the pages that follow are data-driven, either by the incident corpus that is the foundation of this publication, or by non-incident data sets contributed by several security vendors.
This report is built upon analysis of 41,686 security incidents, of which 2,013 were confirmed data breaches. We will take a look at how results are changing (or not) over the years as well as digging into the overall threat landscape and the actors, actions, and assets that are present in breaches. Windows into the most common pairs of threat actions and affected assets also are provided. This affords the reader with yet another means to analyze breaches and to find commonalities above and beyond the incident classification patterns that you may already be acquainted with.
Fear not, however. The nine incident classification patterns are still around, and we continue to focus on how they correlate to industry. In addition to the nine primary patterns, we have created a subset of data to pull out financially-motivated social engineering (FMSE) attacks that do not have a goal of malware installation.
【更多详情,请下载:2019年数据泄露调查报告】

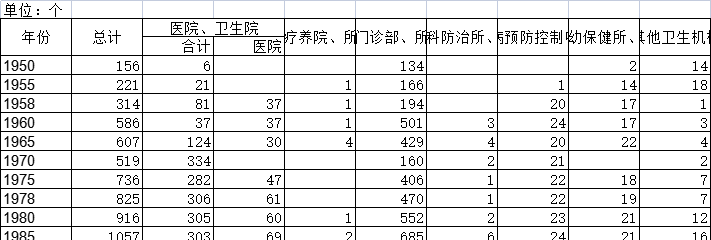 截至2020年宁夏回族自治区规模以上服务业企业调查主要数据该数据包含了截至2020年宁夏回族自治区规模以上服务业企业调查主要数据。1950年总计为156个。2020年发布时间:2022-07-25
截至2020年宁夏回族自治区规模以上服务业企业调查主要数据该数据包含了截至2020年宁夏回族自治区规模以上服务业企业调查主要数据。1950年总计为156个。2020年发布时间:2022-07-25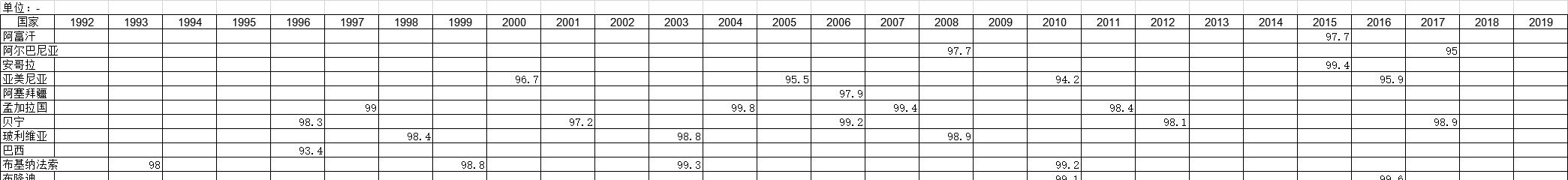 1992-2019年全球受访国家男性调查的家庭答复率的调查统计数据本数据记录了1992-2019年全球受访国家男性调查的家庭答复率的调查统计数据。调查内容为男性调查的家庭答复率。1992-2019年发布时间:2021-01-27
1992-2019年全球受访国家男性调查的家庭答复率的调查统计数据本数据记录了1992-2019年全球受访国家男性调查的家庭答复率的调查统计数据。调查内容为男性调查的家庭答复率。1992-2019年发布时间:2021-01-27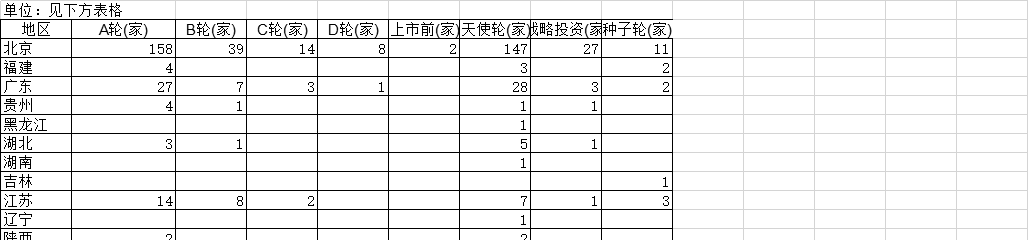 2013-2019年数据服务领域在全球各地区投资公司的轮次情况该统计数据包含了2013-2019年数据服务领域在各地区投资公司的轮次情况。北京A轮公司数量为158家,B轮公司数量为39家,C轮公司数量为14家。2019年发布时间:2020-07-16
2013-2019年数据服务领域在全球各地区投资公司的轮次情况该统计数据包含了2013-2019年数据服务领域在各地区投资公司的轮次情况。北京A轮公司数量为158家,B轮公司数量为39家,C轮公司数量为14家。2019年发布时间:2020-07-16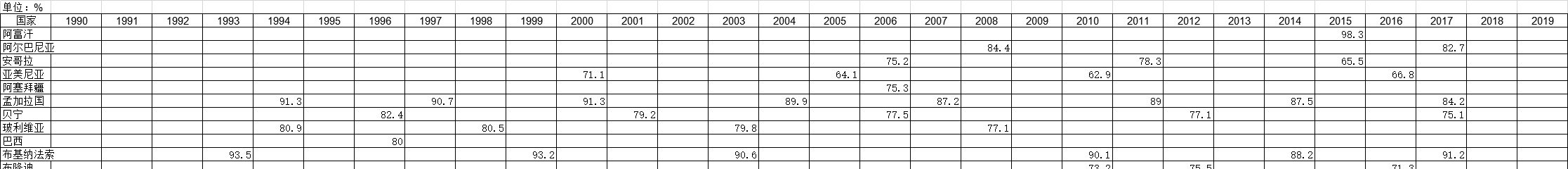 1990-2019年全球受访国家男户主家庭的调查统计数据本数据记录了1990-2019年全球受访国家男户主家庭的调查统计数据。调查内容为男性户主家庭的百分比。1990-2019年发布时间:2021-01-27
1990-2019年全球受访国家男户主家庭的调查统计数据本数据记录了1990-2019年全球受访国家男户主家庭的调查统计数据。调查内容为男性户主家庭的百分比。1990-2019年发布时间:2021-01-27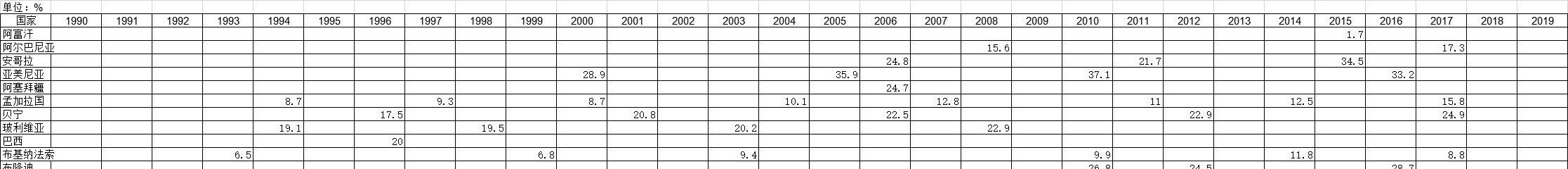 1990-2019年全球受访国家女户主家庭的调查统计数据本数据记录了1990-2019年全球受访国家女户主家庭的调查统计数据。调查内容为以妇女为户主的家庭百分比。1990-2019年发布时间:2021-01-27
1990-2019年全球受访国家女户主家庭的调查统计数据本数据记录了1990-2019年全球受访国家女户主家庭的调查统计数据。调查内容为以妇女为户主的家庭百分比。1990-2019年发布时间:2021-01-27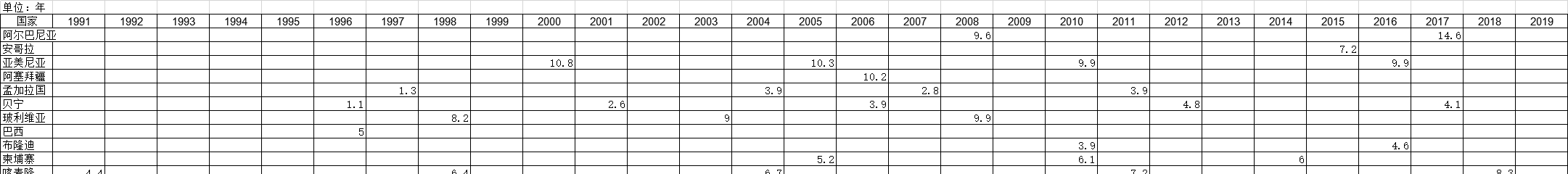 1991-2019年全球受访国家完成学历的中位数[男]的调查统计数据本数据记录了1991-2019年全球受访国家完成学历的中位数[男]的调查统计数据。调查内容为男子接受教育的平均年数。1991-2019年发布时间:2021-01-27
1991-2019年全球受访国家完成学历的中位数[男]的调查统计数据本数据记录了1991-2019年全球受访国家完成学历的中位数[男]的调查统计数据。调查内容为男子接受教育的平均年数。1991-2019年发布时间:2021-01-27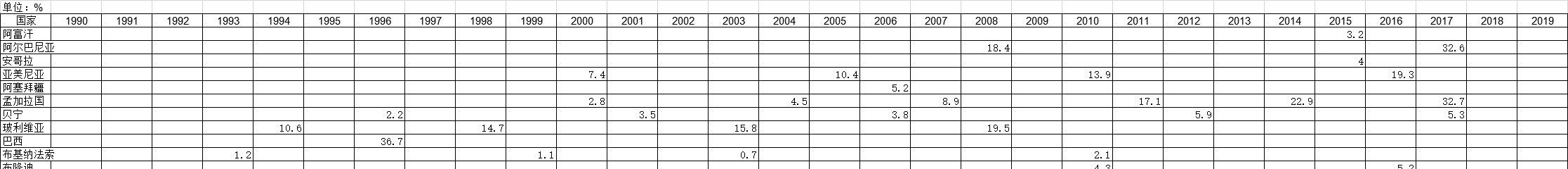 1990-2019年全球受访国家剖宫产的调查统计数据本数据记录了1990-2019年全球受访国家剖宫产的调查统计数据。调查内容为剖宫产调查前的五(或三)年活产婴儿所占百分比。1990-2019年发布时间:2021-01-27
1990-2019年全球受访国家剖宫产的调查统计数据本数据记录了1990-2019年全球受访国家剖宫产的调查统计数据。调查内容为剖宫产调查前的五(或三)年活产婴儿所占百分比。1990-2019年发布时间:2021-01-27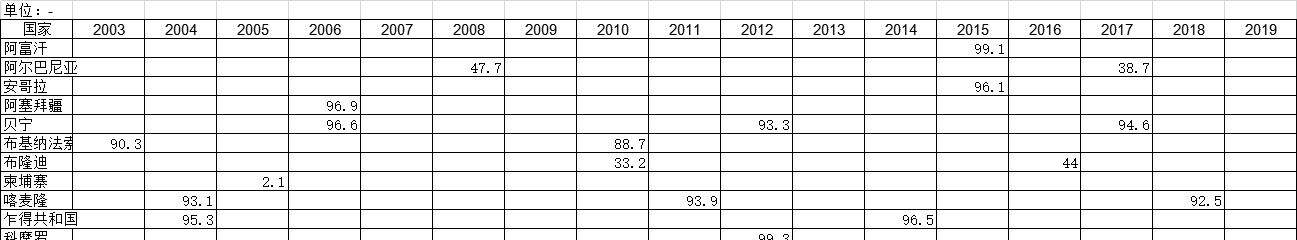 2003-2019年全球受访国家男子割礼的调查统计数据本数据记录了2003-2019年全球受访国家男子割礼的调查统计数据。调查内容为报告被割礼的男性比例。2003-2019年发布时间:2021-01-20
2003-2019年全球受访国家男子割礼的调查统计数据本数据记录了2003-2019年全球受访国家男子割礼的调查统计数据。调查内容为报告被割礼的男性比例。2003-2019年发布时间:2021-01-20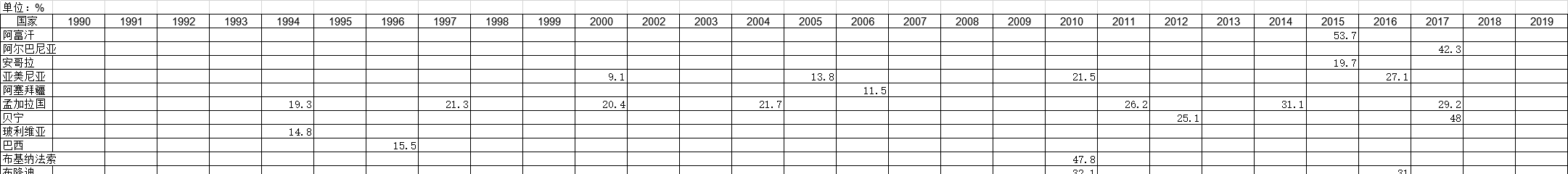 1990-2019年全球受访国家停止怀孕的调查统计数据本数据记录了1990-2019年全球受访国家停止怀孕的调查统计数据。调查内容为在调查开始前的五年中,避孕方法停止使用的百分比。1990-2019年发布时间:2021-01-27
1990-2019年全球受访国家停止怀孕的调查统计数据本数据记录了1990-2019年全球受访国家停止怀孕的调查统计数据。调查内容为在调查开始前的五年中,避孕方法停止使用的百分比。1990-2019年发布时间:2021-01-27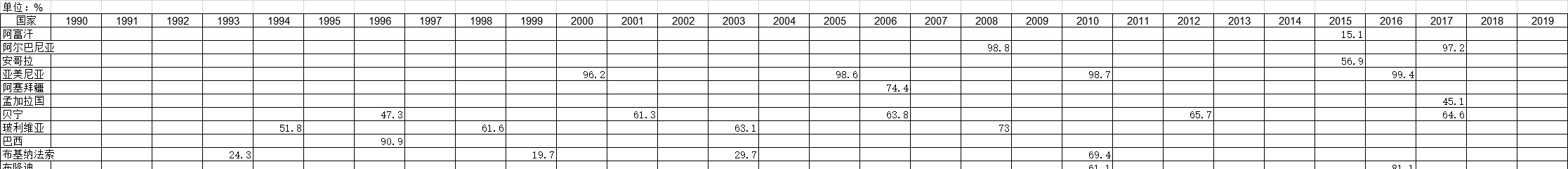 1990-2019年全球受访国家报告孩子的出生体重的调查统计数据本数据记录了1990-2019年全球受访国家报告孩子的出生体重的调查统计数据。调查内容为在调查之前的五(或三)年中有活产百分比,并通过数字报告出生体重。1990-2019年发布时间:2021-01-20
1990-2019年全球受访国家报告孩子的出生体重的调查统计数据本数据记录了1990-2019年全球受访国家报告孩子的出生体重的调查统计数据。调查内容为在调查之前的五(或三)年中有活产百分比,并通过数字报告出生体重。1990-2019年发布时间:2021-01-20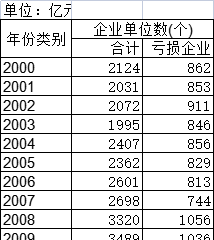 截至2021年云南省规模以上工业企业主要经济数据该数据包含了截至2021年云南省规模以上工业企业主要经济数据。2000年企业单位数为2124个。2021年发布时间:2022-03-30
截至2021年云南省规模以上工业企业主要经济数据该数据包含了截至2021年云南省规模以上工业企业主要经济数据。2000年企业单位数为2124个。2021年发布时间:2022-03-30 1985-2019年全球受访国家小儿腹泻的调查统计数据本数据记录了1985-2019年全球受访国家小儿腹泻的调查统计数据。调查内容为在调查前五(或三年)内出生的儿童在调查前两周内腹泻的百分比。1985-2019年发布时间:2021-01-20
1985-2019年全球受访国家小儿腹泻的调查统计数据本数据记录了1985-2019年全球受访国家小儿腹泻的调查统计数据。调查内容为在调查前五(或三年)内出生的儿童在调查前两周内腹泻的百分比。1985-2019年发布时间:2021-01-20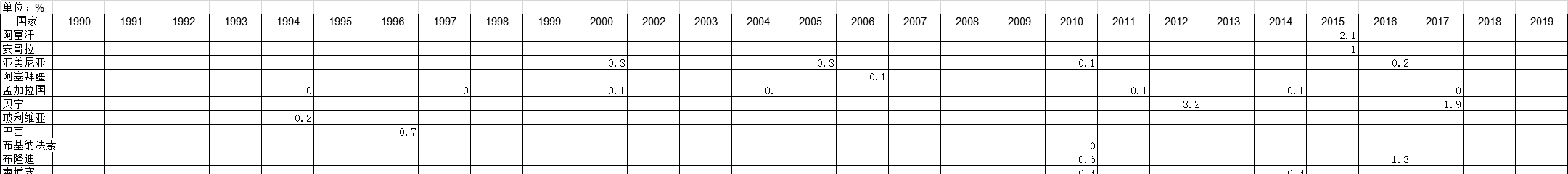 1990-2019年全球受访国家女人死于绝症的调查统计数据本数据记录了1990-2019年全球受访国家女人死于绝症的调查统计数据。调查内容为在调查之前的五年中,由于女性致死,终止避孕方法的百分比。1990-2019年发布时间:2021-01-27
1990-2019年全球受访国家女人死于绝症的调查统计数据本数据记录了1990-2019年全球受访国家女人死于绝症的调查统计数据。调查内容为在调查之前的五年中,由于女性致死,终止避孕方法的百分比。1990-2019年发布时间:2021-01-27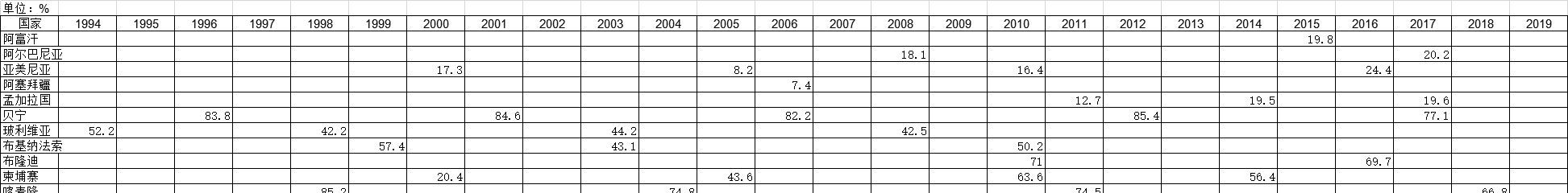 1994-2019年全球受访国家女性自营职业的调查统计数据本数据记录了1994-2019年全球受访国家女性自营职业的调查统计数据。调查内容为自雇人士调查前的12个月内受雇的妇女百分比。1994-2019年发布时间:2021-01-27
1994-2019年全球受访国家女性自营职业的调查统计数据本数据记录了1994-2019年全球受访国家女性自营职业的调查统计数据。调查内容为自雇人士调查前的12个月内受雇的妇女百分比。1994-2019年发布时间:2021-01-27 1985-2019年全球受访国家面试中位数的调查统计数据本数据记录了1985-2019年全球受访国家面试中位数的调查统计数据。调查内容为年度住户访问的中位数。1985-2019年发布时间:2021-02-02
1985-2019年全球受访国家面试中位数的调查统计数据本数据记录了1985-2019年全球受访国家面试中位数的调查统计数据。调查内容为年度住户访问的中位数。1985-2019年发布时间:2021-02-02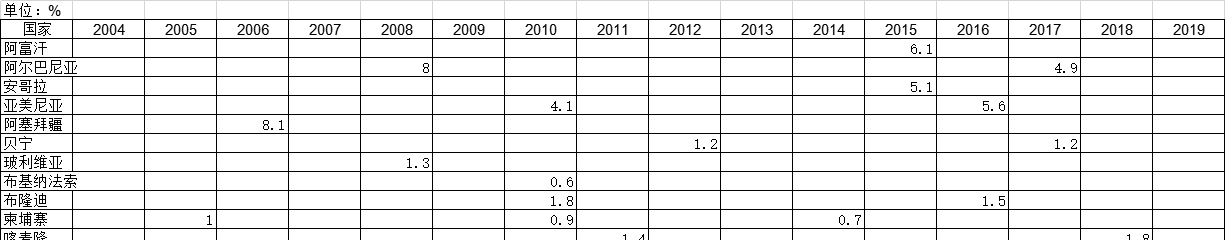 2004-2019年全球受访国家丈夫没有收入的调查统计数据本数据记录了2004-2019年全球受访国家丈夫没有收入的调查统计数据。调查内容为在调查前的12个月中丈夫没有现金收入的已婚或同居妇女所占百分比。2004-2019年发布时间:2021-01-20
2004-2019年全球受访国家丈夫没有收入的调查统计数据本数据记录了2004-2019年全球受访国家丈夫没有收入的调查统计数据。调查内容为在调查前的12个月中丈夫没有现金收入的已婚或同居妇女所占百分比。2004-2019年发布时间:2021-01-20 1985-2019年全球受访国家平均活儿数的调查统计数据本数据记录了1985-2019年全球受访国家平均活儿数的调查统计数据。调查内容为所有妇女的平均存活子女数。1985-2019年发布时间:2021-01-20
1985-2019年全球受访国家平均活儿数的调查统计数据本数据记录了1985-2019年全球受访国家平均活儿数的调查统计数据。调查内容为所有妇女的平均存活子女数。1985-2019年发布时间:2021-01-20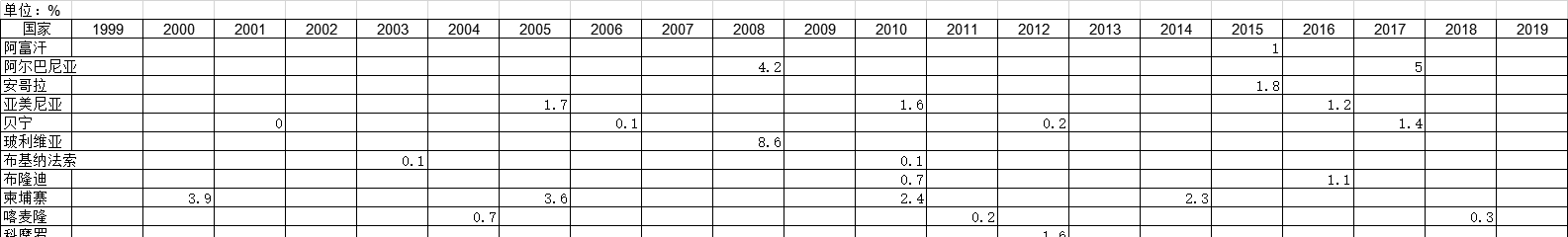 1999-2019年全球受访国家抽烟的妇女的调查统计数据本数据记录了1999-2019年全球受访国家抽烟的妇女的调查统计数据。调查内容为抽烟的女性百分比。1999-2019年发布时间:2021-01-20
1999-2019年全球受访国家抽烟的妇女的调查统计数据本数据记录了1999-2019年全球受访国家抽烟的妇女的调查统计数据。调查内容为抽烟的女性百分比。1999-2019年发布时间:2021-01-20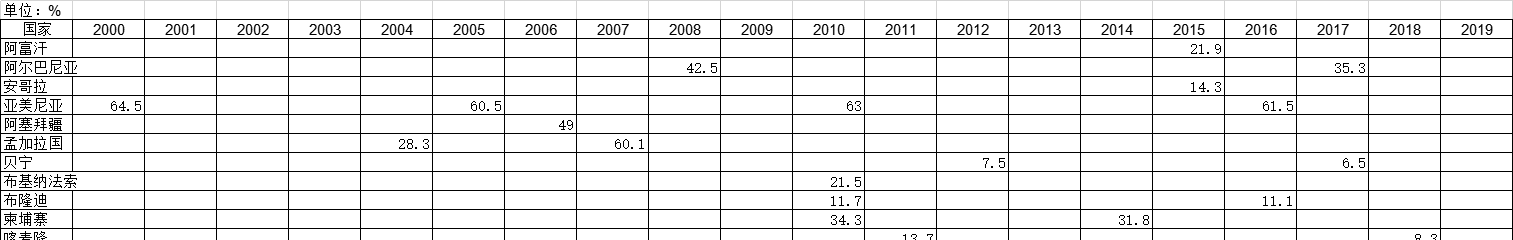 2000-2019年全球受访国家抽烟的男人的调查统计数据本数据记录了2000-2019年全球受访国家抽烟的男人的调查统计数据。调查内容为抽烟的男性百分比。2000-2019年发布时间:2021-01-20
2000-2019年全球受访国家抽烟的男人的调查统计数据本数据记录了2000-2019年全球受访国家抽烟的男人的调查统计数据。调查内容为抽烟的男性百分比。2000-2019年发布时间:2021-01-20 1990-2019年全球受访国家有电家庭的调查统计数据本数据记录了1990-2019年全球受访国家有电家庭的调查统计数据。调查内容为有电家庭的百分比。1990-2019年发布时间:2021-01-27
1990-2019年全球受访国家有电家庭的调查统计数据本数据记录了1990-2019年全球受访国家有电家庭的调查统计数据。调查内容为有电家庭的百分比。1990-2019年发布时间:2021-01-27





